Ransomware: A Guide To Prevention And Solution
The Covid-19 outbreak forced large and small corporations alike to shift from working in-house, protected behind corporate firewalls, to working remotely rendering endpoints more vulnerable than ever.
Ransomware attacks surpassed 2020’s total volume of 304.6 million in just H1 of 2021 (307.6 million), an increase of 151%. To make it worse, 22% (previously 11%) of all cybersecurity incidents in H1 2021 were ransomware attacks. If you are in the US, ransomware has propagated by 185% this year. This has been dubbed as “the digital pandemic”.
Not only is the world facing a physical pandemic but also a digital one. Bad actors are always on the lookout for weak points and a global pandemic hasn’t deterred them in the least.
There are always preemptive cybersecurity measures that you can employ.
How Does One Get Infected With Ransomware?
A cybercriminal can use an array of methods to lure in their unsuspecting victim, the prominent one being phishing (email or text message with an attached file or link where the ransomware resides).
Bad actors generally use social engineering tricks to disguise themselves as legitimate businesses. For example, they can forge an email address with a believable domain such as John.doe@google-support.com even though @google-support.com is not an official address Google agents use, it does sound legitimate.
After the e-mail address is forged, the next step is to copy Google’s branding and style and then send out an email with a link or file which contains the ransomware.
After you or a potential victim receives such an e-mail, if done correctly, the received material is going to look like it was sent by Google, a trusted source. However, when the link is clicked or the file downloaded that’s when things start going south. The ransomware can either run immediately or lay dormant without your knowledge.
How Ransomware Works
After the ransomware infects a system it will inform the victim/s that their data has been encrypted, meaning the victim will not be able to access their files anymore. The cybercriminal will require payment via cryptocurrency in order to shield their identity in exchange for the decryption key.
If not paid within a certain time frame the attacker might increase the required ransom making the situation worse.
Steps You Can Take To Prevent And Solve A Ransomware Attack
- Ransomware relies on you to make a mistake so be an educated and cautious end-user.
- Allow automatic updates for anti-virus and anti-malware solutions.
- Back up data and ensure everything went smoothly
- Isolate your backups
- Employ a business continuity plan (BCP), for when you are breached.
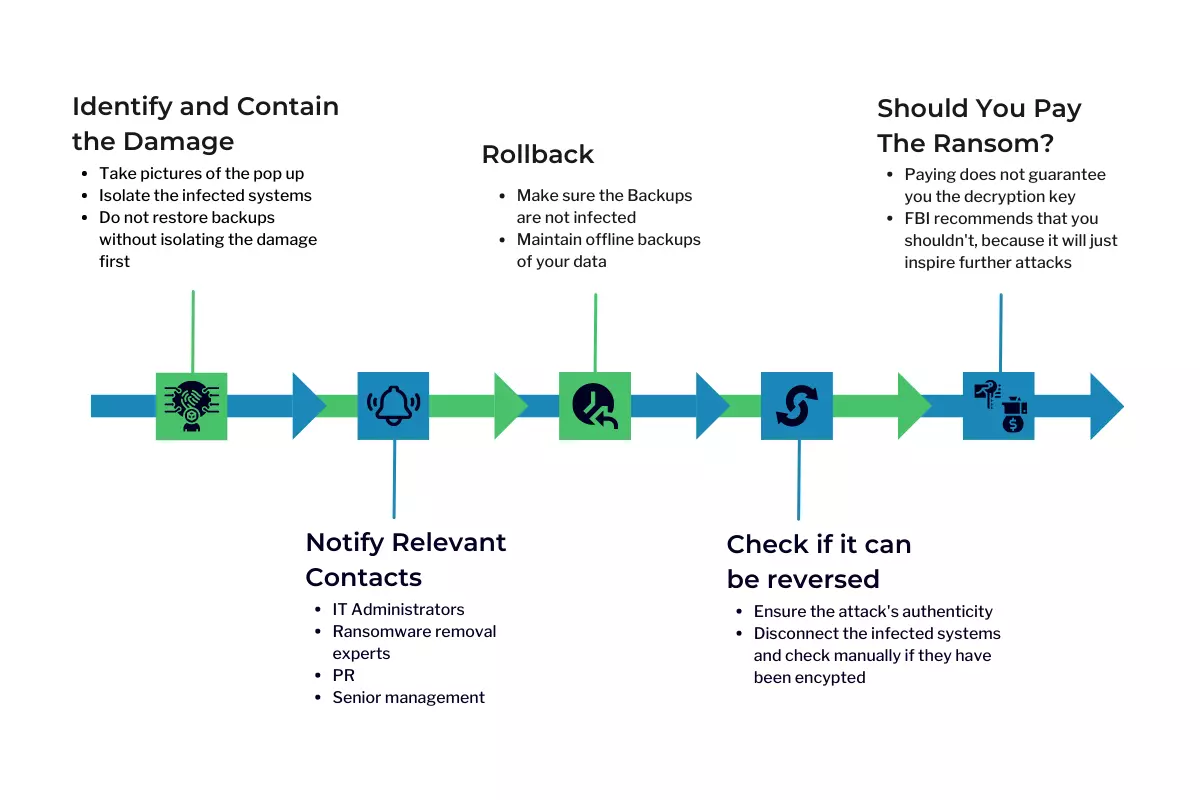
Ransomware Recovery Steps
1. Identify and contain the damage
Act with caution and do not proceed to immediately restore backups; that might make things worse. First, determine what systems, users, and networks were compromised and isolate them from the rest. Also, check what hasn’t been infected and turn off backups.
Take pictures of the popup, specifically the extensions. This will help identify the type of threat.
No matter what you do, do not restore backups without containing and isolating the compromised systems. Otherwise, the ransomware will reinfect the restored machines, or worse it might infect the backups.
2. Notify relevant contacts
If you have an implemented response plan then you should already have a list of people who you should contact such as administrators, ransomware removal experts, PR, senior management, etc.
If no plan was set beforehand, then most security companies will be able to help. However, you might be required to pay extra due to the sudden nature of the issue.
Calling the FBI cybercrime division is not a bad idea either.
3. Rollback
The most efficient solution would be to just reset all compromised assets to their last functional state. First, make sure that the backups have not been infected as well, and be careful not to open a gateway for the attackers to infect your backups.
Offline backups, “air-gapped” storage, and WORM functionality backups are safe from ransomware. Cloud storage vendors (AWS, Microsoft Azure, or even Google) offer long-term backup storage that once written can’t be altered anymore. Leveraging these types of vendors is an effective way of ensuring backup safety.
4. Check if it can be reversed
There are cases when the ransomware is fake. It acts like a real one, asking for payment and notifying you that your files have been encrypted. However, it does not encrypt the files. This bluff relies on the victim to panic and pay the ransom immediately.
So, disconnect the affected systems from the network and try to access those files manually, and ensure whether or not they are encrypted.
If the threat is genuine, take its name and add “decryptor” on Google Search. Sometimes older versions of ransomware are used for which a decryptor already exists. However, double-check the provider’s authenticity as well.
Security vendors sometimes are able to decrypt the files if a solution is not readily available online. Although, that usually happens when Ransomware’s programming is lacking.
5. Should you pay the ransom?
FBI objects to complying with the ransom, the core reason being that paying does not guarantee that the cybercriminals will provide you with the decryption key.
However, in most cases paying the ransom is cheaper than dealing with the operational costs. If paid and everything went smoothly you could restore the lost functionality within hours. On the other hand, it might take weeks if you decide to fight it.
When core data hasn’t been compromised and time is not an issue, then not paying and rebuilding instead might be the better option.
If time is an issue or core data has been compromised, then paying the ransom becomes the better compromise.
Before making the payment, ensure that the attackers can actually decrypt the files. Hiring a ransomware payment expert in this instance would be the safest bet.
Receiving the Ransomware’s decryption key does not imply that you are safe. In fact, now that you have been breached the attackers are aware of your vulnerabilities and target you again. So, starting to enforce your cybersecurity infrastructure is one of the crucial next steps that you should take after being breached.