The 3 Types of Threat Intelligence And Its Cycle
What is Threat Intelligence?
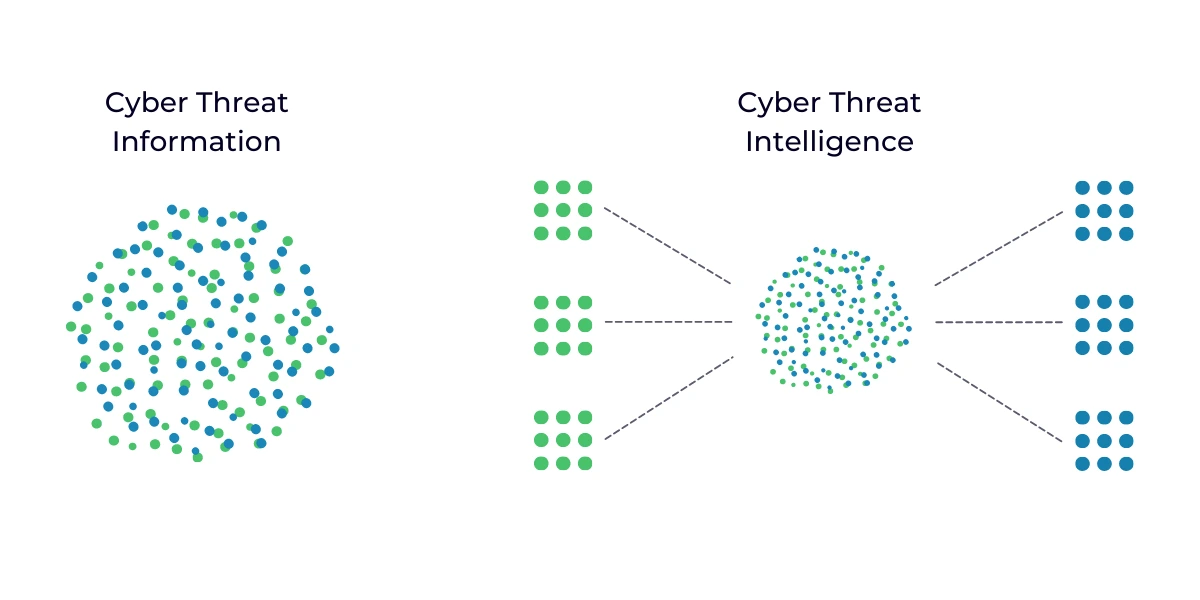
Threat intelligence or cyber threat intelligence is the act of figuring out a bad actor’s motives, targets, and attack behaviors by collecting, analyzing, and processing cyber threat information. Essentially, Threat Intelligence is a method of switching your existing security measures’ behavior from reactive to proactive.
Once cyber threat information is collected, analyzed, and processed, all that information becomes actionable. Hence, it is transformed into cyber threat intelligence.
In short, Threat Intelligence is a way to interpret cyber information into actionable insights.
Why Is Threat Intelligence Important?
Threat Intelligence is needed to gain an insider’s view of the threat landscape and adapt to cybercriminals’ latest strategies and techniques. It enables a proactive approach to secure your sensitive information from insider and outsider threats alike. Additionally, it also provides you with the tools, competence, and policies required to collect, analyze and interpret that information.
Threat intelligence makes you more certain of your security policies and it provides you with the means to adapt to an ever-changing threat landscape.
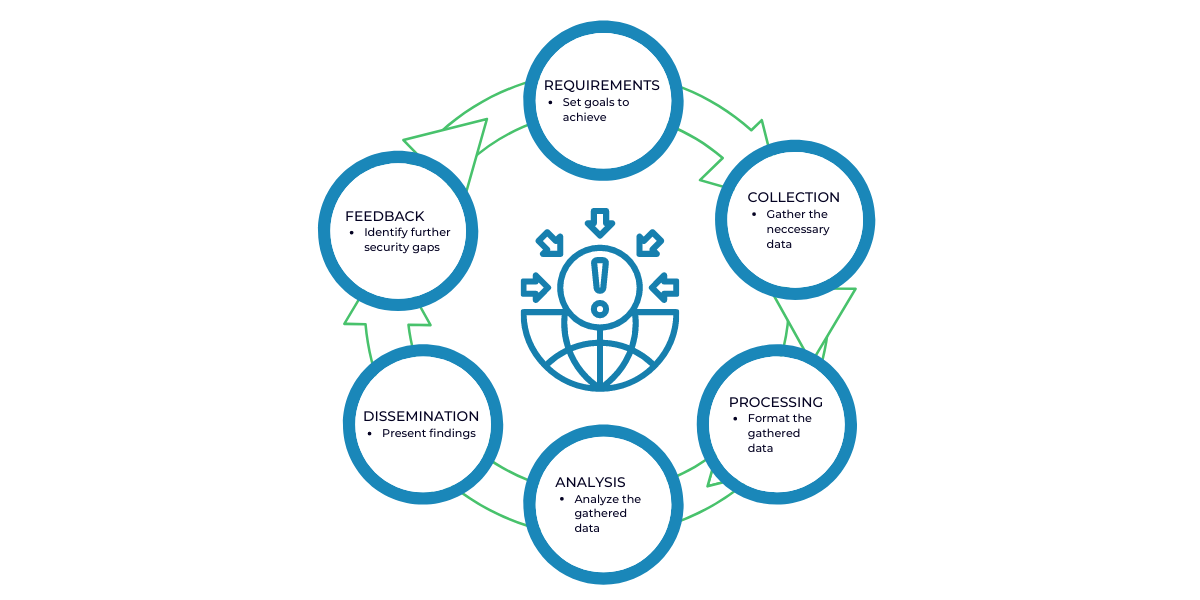
The Cyber Threat Intelligence Lifecycle
Threat intelligence is not an end-to-end procedure, it’s a never-ending circular process. Also known as the threat intelligence cycle.
As such:
- Requirements: At this stage, the allocated team will set the goals and the methodology of the intelligence program based on the pre-set conditions by you or the company in question. This is vital to the intelligence cycle because it sets the roadmap that needs to be followed throughout the cycle.
- Collection: Once the previous step is completed, the team proceeds to seek information and data to fulfill the set requirements and objectives. The team might inquire or analyze info from subject matter experts, cyber traffic logs, relevant forums, social media, or public data sources.
- Processing: As the name suggests, it refers to the process of interpreting data into a format that enables efficient analysis such as organizing data into spreadsheets, file decryption, evaluating data for relevance and reliability, and also, if needed, translation.
- Analysis: At this stage, the now processed data is analyzed to get an answer regarding the objectives set during the requirements stage.
- Dissemination: How the conducted analysis is conveyed to you or the stakeholders in question depends on the audience. Usually, the findings are presented with brevity and without technical jargon in a one-pager or a short slide presentation. So, this step requires the team to convert their analysis into a more comprehensible format and present them.
- Feedback: Once the report has been handed out, now is the time to receive feedback from the concerned parties and determine the configurations and adjustments required to further future intelligence cycles.
Threat Intelligence is a circular process because it constantly identifies previously unknown gaps, which prompts unanswered questions, which, in turn, creates new requirements, and the need to restart the intelligence cycle arises.
What Are The Types Of Threat Intelligence?
Cyber threat intelligence often takes into account the actors, intent, and their capability while considering their TTP ( techniques, tactics, and procedures), their motives, and target access. Through this analysis, threat intelligence enables you to make strategic, operational, and tactical evaluations.
Strategic intelligence: Strategic cyber intelligence provides you with high-level factors that contribute to cyber-attacks such as geopolitical conditions. It creates a general picture of the motives and the risks that malicious cyber threats pose. So, by identifying trends, patterns, and emerging global threats, strategic threat intelligence forms an idea about the potential actors, tools, and TTPs to create and implement policies that provide timely warnings.
Operational/Technical Intelligence: It is more specific than strategic intelligence and provides insights that can support and improve response operations. Operational cyber intelligence is focused on the technical aspect of guiding and responding to cyber threats.
Tactical Intelligence: This type of intelligence is focused on the near or immediate future, also technical, and locates ICOs (Indicators of Compromise) such as bad IP addresses, URLs, known malicious domains, and file hashes. Essentially, it provides day-to-day operational support for the aforementioned threats. –
A properly applied threat intelligence will enable you to predict and adapt to threats before they even occur. It helps you to determine acceptable business risks, develop controls and budgets, and make staffing and equipment decisions (Strategic intelligence). It guides you through threat response and recovery (Operational intelligence) and improves the validation of indicators (Tactical intelligence).
HybridValley excels at collecting and analyzing cyber threat information to translate it into accurate, timely, and relevant cyber threat intelligence. So, if your cyber security program needs some finetuning reach out to us.